The financial sector ranks second in global cyber incident damage statistics, surpassed only the healthcare industry, according to the 2023 IBM’s Cost of a Data Breach Report. Financial organizations experience losses averaging around $5.9M per cyber incident, exceeding the cross-industry average of $4.45 millionThe sector is a prime target for cybercriminals as they hold a goldmine of sensitive data which can be used for various malicious purposes, like targeted phishing attacks or financial fraud. Moreover, cybercriminals can directly steal money from financial institutions through various means, like wire transfers, account takeovers, and ATM skimming. As they also manage fund access, financial institutions are often willing to pay hefty ransoms to get their critical data back compared to other potential victims
With that being said, banking application security testing plays a pivotal role in keeping financial institutions safe from cyber threats and staying one step ahead of hackers. In this article, we’ll explore everything you need to know to enhance your defense.
Types of security testing for banks
1. Vulnerability testing
With this type of testing, teams usually leverage automated scanning tools to scan systems such as servers, routes, and endpoints against predetermined vulnerabilities
During a vulnerability assessment, you can categorize identified security weaknesses based on their type, severity level, etc., based on these frameworks:
- OWASP Top 10 Application Security Risks.
OWASP Top 10 Application Risks.
Open Web Application Security Project (OWASP) Guide.
- Web Application Security Consortium (WASC) Threat Classification.
- Common Vulnerability Scoring System (CVSS).
2. Penetration testing
Penetration testing entails replicating the techniques employed by a real-world attacker to gain access to a company’s data, applications, or IT infrastructure. The objective of penetration testing services is to pinpoint security vulnerabilities within an IT environment, assess their potential impact, and provide guidance for remediation.
3. Security Code Review
Code review encompasses both manual and automated examination of application source code to identify flaws such as encryption errors, buffer overflows, XSS, and SQL injection vulnerabilities. It can help enhance source code performance, scalability, maintainability, and clarity, while also fortifying software against potential cyberattacks.
4. Compliance Assessment
Conducting a compliance assessment is instrumental in identifying and addressing deficiencies in a company’s policies, procedures, software, and IT infrastructure that are subject to industry-specific or widely applicable regulations such as PCI DSS, HIPAA, GLBA, and GDPR. Compliance assessment services encompass:
- Examination of security and quality assurance policies and procedures
- Assessing employees’ understanding of relevant standards and regulations.
- Perform security testing on software and IT networks.
- Provide remediation guidance and practical assistance to rectify any identified gaps.
5. Software Security Audit
A comprehensive evaluation of software security controls involves examining software protection measures alongside the assessment of information security policies and the cyber resilience of employees.
Here are some popular techniques employed in the process:
- Software Application Security Testing (SAST)
It falls under the category of white box testing, where the security testers are familiar with how the code was built, focusing on testing the application’s actual code. It Identifies common coding vulnerabilities like SQL injection, cross-site scripting, and insecure direct object references.
Can be automated and integrated into the development process, making it a good choice for early detection of vulnerabilities.
- Dynamic Application Security Testing (DAST)
DAST operates as a black-box security testing in which testers are uninformed of the app’s underlying architecture. It’s designed to detect vulnerabilities while the app is in runtime. It can identify vulnerabilities that SAST might miss, such as logic flaws and configuration errors. While it requires more manual effort than SAST, the testing type can be more effective at finding critical vulnerabilities.
- Interactive Application Security Testing (IAST)
IAST combines elements of both SAST and DAST to assess the potential exploitation of known vulnerabilities (SAST) within a live application environment (DAST). These tools leverage knowledge of data and application flow to visualize complex attack scenarios. The resulting test cases are then used iteratively to generate additional test cases, building upon DAST results.
In high-paced DevOps environments, IAST tools demonstrate enhanced efficiency and reduced false positives compared to relying solely on DAST or SAST. The real-time feedback provided during testing equips developers with the intelligence and context necessary to promptly recognize and address vulnerabilities as they emerge. This facilitates quicker remediation, leading to a reduction in the overall time and effort required to rectify security issues within the application, thereby minimizing the likelihood of application-related data or security breaches.
What Features Should a Mobile App Security Testing Tool Include?
When deciding on a mobile app security testing tool, it’s vital to consider a variety of capabilities to guarantee thorough testing and safeguard your banking mobile apps. Here are some crucial features to consider:
- Automation & CI/CD integration
Search for a tool that seamlessly integrates into your CI/CD pipeline with common development tools, including integrated development environments (IDEs), build systems, and continuous integration/continuous deployment (CI/CD) pipelines to enhance the efficiency of the development and testing workflow.
- Customization and configuration
The ability to customize and configure not only enhances flexibility but also enables a more precise alignment of the tool with the specific intricacies of your organization’s security landscape, fostering a tailored and robust security framework.
- Scalability
The tool should remain adept at handling increased workloads, data volumes, and user interactions, all while maintaining optimal performance levels
- Customer support and community
An active user community adds immense value by fostering the sharing of knowledge, best practices, and user-generated scripts or plugins that enrich the functionality of the tool. Moreover, the presence of responsive and knowledgeable customer support from the tool’s provider is crucial for ensuring a positive user experience.
- Detailed reporting
The tool is expected to generate a concise and actionable report detailing identified vulnerabilities, encompassing crucial information on the severity of each issue, potential impact, and recommendations for effective remediation.
Top Mobile Banking App Security Tools
AppKnox
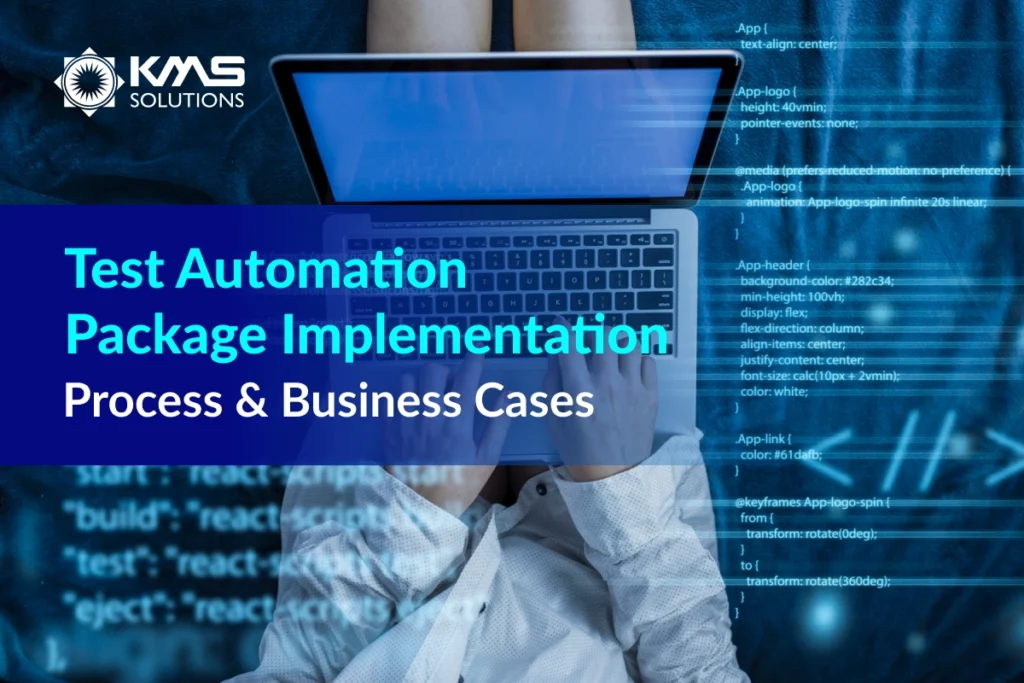
AppKnox Mobile Application Security employs a comprehensive approach that combines SAST, DAST, and API scans to assess the security of your mobile banking app. Following each assessment, AppKnox generates a detailed report highlighting the severity of detected vulnerabilities, their business impact, and any regulatory and compliance issues. This report provides valuable insights into security weaknesses and aids in preparing for necessary remediation measures.
In addition to automated security checks, AppKnox offers manual penetration testing services conducted by a dedicated team of security experts. These professionals assist in consolidating and providing guidance on vulnerabilities identified during the automated testing process. After the security analysis, AppKnox provides a remediation call service, during which their security researchers explain the vulnerability findings, discuss industry best practices, and explore various mitigation methods. This ensures that your mobile applications receive comprehensive attention to enhance their security posture.
Checkmarx
The cloud-native platform integrates a comprehensive range of application security testing (AST) solutions, ensuring the security of your digital transformation throughout every stage of modern financial application development
- Static Application Security Testing (SAST)
- Infrastructure as Code (IaC) Security
- API Security
- Software Composition Analysis (SCA)
- Container Security
- Dynamic Application Security Testing (DAST)
- Supply Chain Security (SCS)
The tool also offers seamless integration with SDLC tools, IDEs, bug-tracking systems, and CI services. It also comes with a unified dashboard to aid in detecting and remediating vulnerabilities across AST solutions via a common workflow. It works for Android, iOS, and Windows Mobile, supporting 50+ languages and 100+ frameworks.
Data Theorem
The platform delivers robust application security testing through vulnerability assessment, compliance testing, static and dynamic analysis, and powerful hacker toolkits. This comprehensive approach enables the identification of threats across every layer of your application stack. Additionally, the platform provides observability and telemetry, actively blocking real-time attacks throughout the application stack. Beyond vulnerability discovery, Data Theorem expedites remediation by offering recommendations and secure code samples, facilitating a quicker response to security findings. Furthermore, it allows for integration with CI/CD tools, facilitating a seamless DevSecOps solution across the release cycle. Currently, the solution covers over 2.8 billion users, including five of the top seven largest banks.
HCL
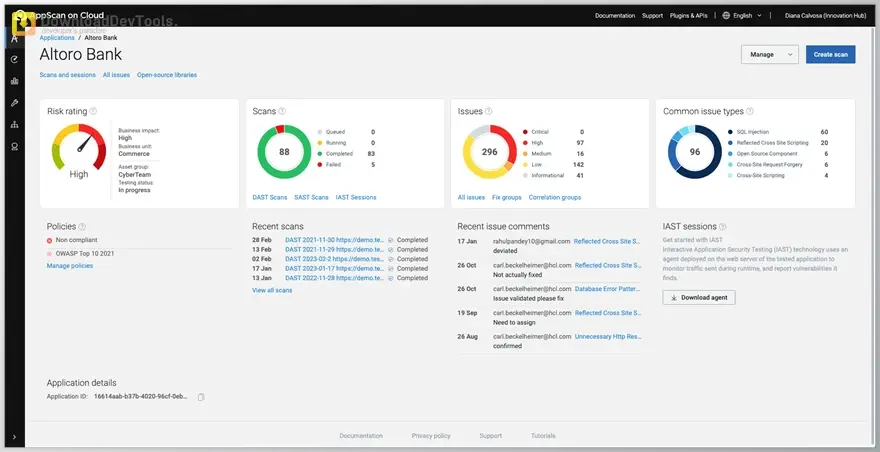
HCL AppScan provides a suite of solutions that empower developers, DevOps, and security teams to identify application vulnerabilities swiftly for prompt remediation throughout every phase of the software development lifecycle:
- DAST
- SAST
- IAST
- SCA
This all-encompassing platform provides various deployment options, such as on-premises, on-cloud, and hybrid solutions. Leveraging machine learning capabilities, HCL AppScan ensures extensive coverage and heightened accuracy in scanning, effectively reducing false positives. Following the analysis of an application, HCL AppScan consolidates and correlates findings from various testing technologies, offering evidence of exploitability and aiding in the prioritization of remediation efforts. Backed by over 20 years of experience, HCL AppScan supports more than 30 code languages, simplifying the process of scanning files.
NowSecure Platform
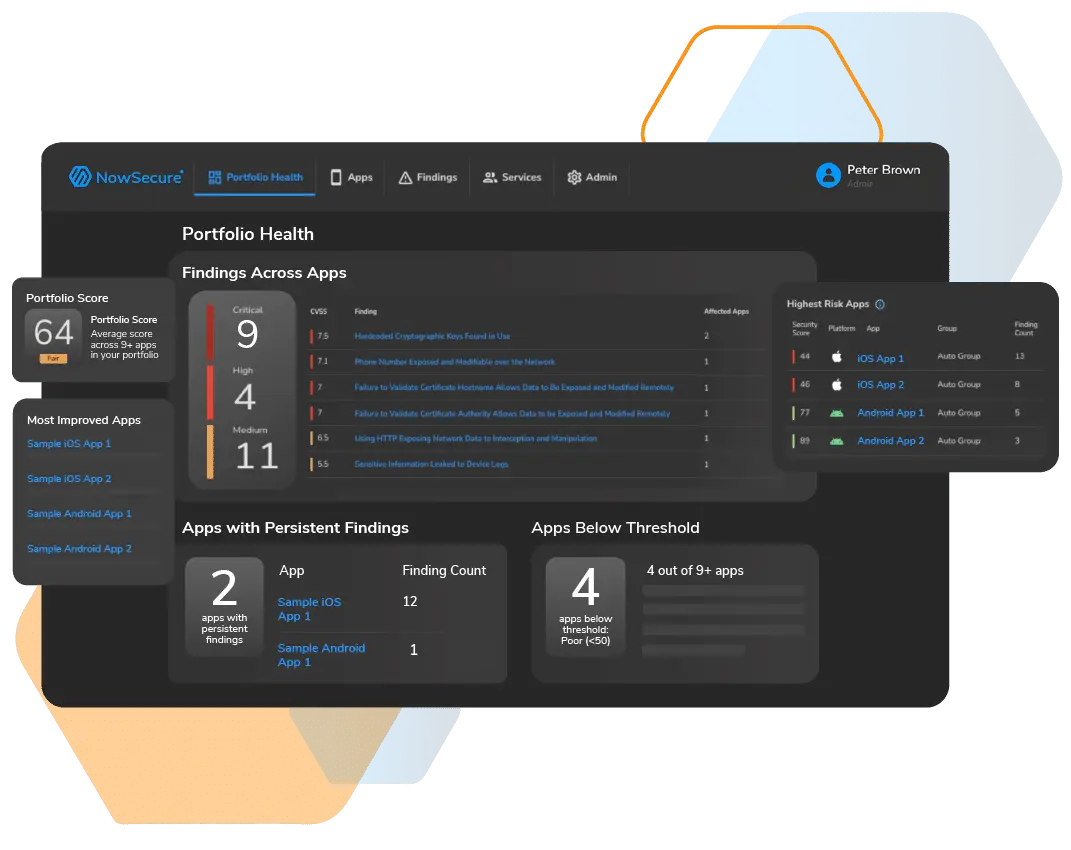
The NowSecure Platform is an all-in-one solution for continuous automated mobile app security testing. for Android and iOS. it excels in identifying security threats, privacy concerns, and compliance gaps across a spectrum of mobile applications, including commercial, business-critical, and custom-developed ones.
The tool offers enhanced flexibility through the NowSecure Command Line Interface (CLI), allowing for more personalized interactions and seamless integration into the development process. It uniquely addresses the intricate infrastructure of modern SDLCs using static analysis, dynamic analysis, interactive testing, and API security analysis. Additionally, it facilitates integration with existing development lifecycle processes through pre-built integrations, open APIs, and a native CLI, fostering a secure development workflow.
Recognizing the diverse nature of mobile apps, the NowSecure Platform empowers teams to tailor testing coverage based on a tiered risk model. This model takes into account the app’s risk profile, threat model, and the team’s budget, ensuring a customized and effective approach to mobile app security.
Keep Your Banking Apps Secure with KMS Solutions
Leveraging hands-on experience with a diverse array of security testing automation tools, our expert team excels in guiding you to select the optimal toolset. Committed to delivering the highest quality service to our clients, we remain vigilant in staying updated on advanced hacking techniques and providing insightful advice on effective corrective measures.
In the dynamic landscape of the financial sector, where compliance is paramount, our security engineers are actively involved in identifying and addressing gaps related to data protection standards. This includes compliance with stringent regulations such as HIPAA, PCI DSS, GDPR, and others.
To strengthen your banking software’s security framework, explore our Banking Software Development services today! Elevate your security measures today by reaching out to our knowledgeable experts.